Laptop security configuration for small business is a complete management policy package ensuring safety and security for the lifecycle of the laptop asset.
If Attention Is Given To Creating And Implementing Strong Policies For Laptop Security, Small Businesses Will Position Themselves To Protect Their Company And Their Employees.
Key Takeaways
- Regular Audits and Updates: Conduct periodic security audits and updates to maintain compliance and adapt to evolving threats.
- Comprehensive Security: Securing laptops is essential for a robust business security strategy, protecting sensitive data and trade secrets.
- Tailored Management Systems: Develop a customized laptop security management system that aligns with your specific business needs and operational environment.
- Best Practices Implementation: Regularly apply firmware and OS updates, use encryption, and conduct data sanitization to protect against data theft.
- Employee Awareness and Training: Ensure all employees are informed about security policies and engage in regular training to foster a security-conscious culture.
- Policy Customization and Integration: Customize security policies to fit your business model and integrate them with existing security measures for cohesive protection.
- Key Takeaways
- Laptop Security Configuration: A Comprehensive Guide for Small Businesses
- Create A Laptop Security Management System
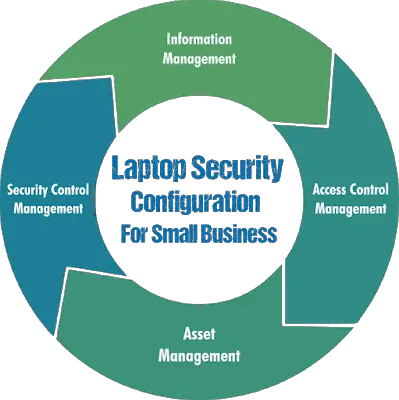
- Laptop Security Configuration Policies
- Information Management
- Access Control Management
- Asset Management
- Security Incident Management
- The Importance of Applying Firmware Updates
- Laptop Security Configuration Best Practices
- Essential Laptop Security Tools for Small Businesses
- Summary
Laptop Security Configuration: A Comprehensive Guide for Small Businesses
Securing laptops is one part of a larger and more complex security posture for small businesses. Procedures and policies need to be designed and enforced to cover all aspects of business security.
Here’s how you can fortify your laptop security setup effectively:
- Understand the Importance:
- Comprehensive Security: Recognize that laptop security is just one part of your overall business security strategy. It should integrate seamlessly with other security measures.
- Data Protection: Protecting confidential data on laptops is paramount. Small businesses often struggle with this, leading to vulnerabilities.
- Common Challenges:
- Lack of Awareness: Many small businesses underestimate the risks associated with inadequate laptop security.
- Resource Limitations: Limited resources and technical expertise can hinder the implementation of effective security measures.
- Data Backup Neglect: Alarmingly, 47% of small to medium-sized businesses do not regularly back up their data, increasing the risk of data loss.
- Developing Security Policies:
- Policy Design: Create clear, comprehensive security policies tailored to your business needs. These should cover all aspects of laptop usage and data protection.
- Employee Training: Ensure all employees understand and adhere to these policies. Regular training sessions can help reinforce security practices.
- Practical Steps for Enhancing Laptop Security:
- Data Encryption: Implement encryption for sensitive data to prevent unauthorized access.
- Regular Updates: Schedule regular updates for operating systems and security software to patch vulnerabilities.
- Access Controls: Use strong passwords and two-factor authentication to protect access to laptops.
- Backup Solutions: Establish a reliable data backup system, ensuring critical information is stored securely and can be restored if needed.
- Enforcement and Review:
- Policy Enforcement: Consistently enforce security policies through monitoring and audits.
- Continuous Improvement: Periodically review and update your security policies to adapt to new threats and technologies.
By acknowledging the essential role of laptop security and implementing these strategies, small businesses can significantly mitigate risks and protect their valuable assets. Remember, a proactive approach to security not only safeguards your business but also builds trust with clients and stakeholders.
Follow-Up Question and Answer
Q: How should small businesses start implementing a laptop security strategy?
A: Start by assessing the risks unique to your business to pinpoint vulnerabilities. Focus on simple steps first: update antivirus software, activate firewalls, and enforce strong passwords.
Regularly update software to guard against new threats. Also, train employees on security practices and set clear policies. This foundation helps build a flexible security plan that grows with your business needs. For more tailored advice, consider consulting a cybersecurity expert.
Acknowledge laptop security policies are essential to your business.
Create A Laptop Security Management System
Laptops are increasingly important tools to any business today. Employees are more mobile than ever and need access to mobile devices constantly.
Generally, best practices across the industry are adopted and customized for each particular business use. For example, you can customize an asset management procedure so it covers mobile devices in your business environment.
This guide will deal in the area of laptop security for the user to adapt to their business model. It’s important that all employees understand and buy into the security plan.
Repeatable processes should be well documented and explained to all employees. In addition, routine training for all is a critical element of any security policy.
- Understand the Role of Laptops:
- Essential Business Tools: Recognize the critical role laptops play in daily operations and the importance of securing them.
- Employee Mobility: With increasing mobility, secure access to mobile devices is a necessity.
- Adopt and Customize Best Practices:
- Industry Standards: Start by adopting industry best practices for security.
- Customization: Tailor these practices to fit your specific business environment. For instance, customize asset management procedures to include laptops.
- Developing a Security Plan:
- Comprehensive Strategy: Create a security plan that integrates with your broader business security policies.
- Employee Engagement: Ensure that all employees understand and support the security plan to foster a security-conscious culture.
- Documenting and Implementing Processes:
- Clear Documentation: Document repeatable security processes thoroughly. This clarity helps in maintaining consistency and accountability.
- Policy Segments: Break down laptop security into individual policy segments that align with overall business security strategies.
- Training and Awareness:
- Routine Training: Conduct regular training sessions to keep employees informed about security protocols and updates.
- Critical Element: Routine training is vital for reinforcing security measures and ensuring adherence to policies.
- Written Procedures and Policies:
- Equally Important: Small businesses should recognize that written procedures are as crucial as in larger corporations.
- Comprehensive Coverage: Follow the FCC’s guidelines to cover everything from initial laptop deployment to end-of-life asset disposal.
By implementing these steps, small businesses can create an effective laptop security management system that not only protects their assets but also boosts overall organizational security.
I will break laptop security down into individual policy segments. Again, these should be subsets of broader policies in regard to your business security.
Small businesses may not realize that written procedures and policies are just as important as in larger corporations. The FCC convened a round table and came up with security tips for small businesses. This is an umbrella approach covering start to finish, meaning initial laptop rollout to end-of-life asset disposal.
Also, be sure to read my other top articles:
Laptop Security Configuration Policies
Create these individual policy go-to documents for securing laptops, and ensure every employee reads and acknowledges them. These policies cover the life of the laptop asset and can be stand-alone documents or addendums to current security procedures. See the small business security plan template I created below and customize yours to suit.
- Develop Individual Policy Documents:
- Comprehensive Coverage: Each policy should cover all aspects of laptop security, from acquisition to disposal.
- Lifecycle Management: Ensure the policies address each stage of the laptop’s lifecycle to maintain security consistently.
- Employee Awareness and Acknowledgment:
- Mandatory Reading: Require all employees to read and acknowledge these security policies. This step is crucial for building a security-conscious workforce.
- Regular Updates: Keep employees informed about any updates or changes to the policies.
- Integration with Existing Security Measures:
- Standalone or Addendum: Decide whether these policies will be standalone documents or integrated as addendums to existing security procedures.
- Alignment with Business Security: Ensure these policies align with broader business security strategies for cohesive protection.
- Customization for Specific Needs:
- Tailored Policies: Customize the policies to suit your business environment and specific operational needs.
- Template Utilization: Use templates, such as a small business security plan, and modify them to meet your unique requirements.
- Policy Implementation:
- Clear Guidelines: Provide clear, actionable guidelines within each policy to facilitate easy implementation by employees.
- Monitoring and Enforcement: Establish processes to monitor compliance and enforce adherence to the policies.
By following these steps, small businesses can create effective laptop security configuration policies that protect their digital assets while empowering employees to understand and follow security protocols.
Information Management
Laptop Security Starts With The Employees.
Information Management generally deals with the ownership and distribution of data or information from start to finish. In tailoring this policy to be laptop-specific, we’ll define it as laptop data and information.
Create a written Information Management Laptop Policy that sets expectations for all employees to know and follow in regard to laptop security.
In your Information Management Laptop Policy, describe the actions required to protect the types of data your organization deems sensitive, such as personal information.
- Encrypt laptop hard drives for personal sensitive data or higher. Some OS’s have built-in encryption programs. Make sure to enable these and use them if available, if not, consider investing in one for your business.
- Install virus protection software and malware removal tools. Set the same schedule for every laptop to run virus protection and malware programs.
- Apply OS updates on a set schedule, monthly for example. Updating your software with the latest patches protects it from vulnerabilities.
- Unsolicited E-Mails and Phishing attempts. Opening suspicious emails or clicking improper links is one of the most widely used tools hackers use to gain access. Teach and remind employees that when in doubt, do not open or click such emails. Employ 2-Step authentication wherever it is available and possible.
- Apply firmware updates as needed, such as twice yearly. An IT person in the business is a good point person to handle this task. This person can check and install BIOS and firmware updates on all laptops. Keep a spreadsheet of laptop serial numbers and date of updates. See below for more on the importance of updating firmware.
- Use strong WiFi passwords. At the WiFi router, enable the highest level of security available, and use a strong password.
- Enable and use the OS firewall. Windows OS has its firewall enabled by default. Check the settings and set to Home, Office, Public network.
- Make backup copies of laptop data to store securely. If a laptop is lost or stolen, having backed up data to restore on a replacement will come in handy. You will need to decide on the solution that works in your situation. Perhaps USB drives will be enough or external drives. Either way, protect these devices and store them securely. Best practice says to keep multiple backups and ensure one of these backups is off-line at all times.
- Erase all data from laptops before disposing of them. It’s easy to download a data erasing program to run on all laptops before getting rid of them. This just makes sense to use.
Employee buy-in is crucial for a successful Information Management Policy.
Also read: Lenovo Yoga Book 9i: Specs, Features, and Buying Insights
Access Control Management
Minimize The Risk To Employee Laptops.
Access Control Management’s overall scope covers Authentication, Authorization, and Accountability.
We’ll tailor the Access Control Management Policy for our purposes to be laptop-specific. We’ll define this policy to include:
- User verification for laptop access
- What the user is authorized to access
- How the company expects the user to behave while accessing the laptop and data.
It’s good practice to include in the Access Control policy your audit procedure.
State when and how audits will be performed, such as periodic checks for password rules.
- Require every laptop to have strong passwords, including power-on and OS passwords. Passwords should be at least 8 characters long, a mixture of upper and lower case letters, and make use of a special character or number.
- Administrative passwords should not be used. They allow full access to everything which is dangerous on mobile laptops that could get lost or stolen.
- Require password changes. State in your laptop security policy that passwords must be changed every 90 days. Do not allow reusing of old passwords.
- No unauthorized software. Do not allow unauthorized software to be installed on business laptops. This potentially allows exposure to your network and data.
- Set expectations early. Create policy documentation detailing expected behaviors in regard to secure laptop use and set reasonable penalties for failure to follow.
Access Control should be taken seriously as more bad actors are on the internet trying to steal your company’s data and information.
Asset Management
Protect Laptops.
An Asset Management For Laptops Policy will help your business efficiently track the life cycle of every laptop you own, from purchase to disposal.
This doesn’t just let you know who has what, but can also track OS level, firmware release, and the age of their laptop.
This policy should direct the asset management person to maintain current up-to-date records for proper laptop security.
- Record the purchase date and specs. Your small business needs to know when the laptop was bought, what laptop it was bought, and the details of each laptop.
- Track the laptop serial number to the employee currently in possession of the laptop. Data is king, stay ahead of the curve with complete record management.
- Record operation system levels. So you know what operating system level each laptop is currently running and what patches and updates might b needed.
- Record firmware levels. So you know what updates are needed to be included in the scheduled update policy.
- Create a refresh and disposal schedule. Set an age limit for laptops. Prepare by ordering new laptops and refreshing old and outdated ones. Erase the hard drives of all data prior to disposing of the old laptops.
Robust record keeping equates to laptop security. Keep records up-to-date.
Security Incident Management
Laptop Security Failures.
Security incident management concerns itself with identifying and managing threats and or failures. As well as then analyzing these security incidents to help improve the overall security posture going forward.
Your small business Laptop Security Incident Policy should allow you to respond quickly to mitigate and protect your data. An incidence response plan for small businesses needs a reporting chain of command to be in place and includes a managing supervisor.
- Report every security breach and incident. Each employee is responsible for following the policies of your small business. Any deviation or security incident has to be reported to management. Remediation steps should be outlined in this policy. For example, if a laptop is lost or stolen, determine if you have data exposure. Is it appropriate to remove that user’s access or change the network password for them, etc?
- Develop a post-incident analysis. You simply need to learn from the incident and put your small business in a better position in the future.
- Determine possible impact and severity. How does the loss of the employee’s laptop impact the business? Was there a failure in following the written policies?
SophosLabs reports seeing more than 100,000 unique malicious software samples every single day.
A Laptop Security Incidence Policy has to stress the importance of taking quick remediation actions.
The Importance of Applying Firmware Updates
Traveling employees, especially those that travel overseas, are potential targets of hackers, scammers, and thieves.
The opportunity to access an organization’s private data has bad actors coming out of the woodwork. Firmware attacks are on the rise and pose a difficult-to-detect risk. Just as with applying software updates on a set schedule, make sure to keep laptop firmware updated as well.
According to Eclypsium.com “2019 had the most firmware vulnerabilities ever discovered, marking a 43% rise over the previous record in 2018, and a staggering growth of 750% since 2016.“
Laptop Security Configuration Best Practices
If your company is concerned with the potential theft of trade secrets or any of its data, follow these best practices:
- Apply all firmware updates on laptops, as well as OS updates
- Provide loaner laptops to employees traveling overseas
- Limit the types of data on traveling laptops
- Encrypt the hard drives of these laptops
- Wipe/Erase the data and reinstall an OS on these laptops
- Regular Updates:
- Firmware and OS Updates: Consistently apply all available firmware and operating system updates to ensure your laptops are protected against the latest vulnerabilities.
- Secure Travel Practices:
- Loaner Laptops: Provide employees with loaner laptops specifically for overseas travel, reducing the risk of compromising critical business data.
- Data Limitation: Limit the types of data stored on laptops taken on business trips, ensuring only essential information is accessible.
- Data Encryption:
- Hard Drive Encryption: Encrypt the hard drives of all laptops to protect data in the event of loss or theft. Encryption is a powerful tool for safeguarding sensitive information.
- Data Sanitization:
- Wipe and Reinstall: Regularly erase all data from traveling laptops and reinstall the operating system. This step ensures any residual data is securely removed.
- Ongoing Audits and Compliance Checks:
- Security Audits: Conduct periodic audits of your laptop security configurations to verify compliance with your security policies and make necessary adjustments.
Implementing these practices significantly mitigates the risk of data breaches and enhances your organization’s overall security. While no strategy offers absolute protection, these steps are vital in building a strong defense against potential threats.
Periodic laptop security configuration audits and checks will help with compliance.
Essential Laptop Security Tools for Small Businesses
In the digital age, safeguarding your business’s sensitive data requires a robust set of security tools. Here are some key laptop security tools every small business should consider integrating into their security strategy:
- Antivirus Software: This is your first line of defense against malware, viruses, and other malicious threats. Antivirus programs continuously scan and monitor your system for suspicious activities, helping to prevent data breaches before they occur.
- Firewalls: Acting as a barrier between your network and potential threats from the internet, firewalls control incoming and outgoing network traffic based on predetermined security rules. This ensures that unauthorized access is blocked while allowing legitimate traffic.
- Encryption Tools: By encrypting the data on your laptops, you ensure that even if devices are lost or stolen, the data remains inaccessible without the correct decryption key. Encryption tools are crucial for protecting sensitive business information.
- Virtual Private Networks (VPNs): VPNs create a secure connection to another network over the internet, which is particularly useful for employees working remotely or accessing company data offsite. They help keep data secure by encrypting internet traffic and masking the user’s IP address.
- Device Management Solutions: These tools allow you to remotely monitor, manage, and secure laptops across your business. They provide features such as remote wipe capabilities, software updates, and compliance monitoring, ensuring all devices adhere to company security policies.
Implementing these tools not only strengthens your laptop security but also complements your overall security policies. When used together, they create a comprehensive defense strategy that protects your data and ensures compliance with industry standards.
Summary
Use the laptop security configuration for small business policies you’ve newly created to have security awareness training for all employees. Any small business security policy should include details on your company’s laptop asset posture.
The goal is for everyone to have the same understanding and knowledge about what is required of them in regard to laptop security for your small business.
You want to motivate employees toward a common goal with doable, repeatable processes and policies. In addition, it’s also important to periodically have reviews of these policies, update them as needed, and have refresher meetings for employees.
Here is where audits come into play. Perform laptop security checks to ensure compliance with your written policies.
As employees become more mobile, developing written laptop security configuration policies for your small business has become increasingly important. Taking the time to develop and maintain a strong posture for laptop security will prove beneficial now and in the future.

J.S. is the owner, content creator, and editor at Upgrades-and-Options.com. I’ve worked in the IT and Computer Support field for over 20 years. The server hardware in my computer labs has mostly been IBM, but I’ve supported Dell, HP, and various other hardware. In addition, as part of my lab administrator responsibilities, I’ve learned, supported, and repaired/upgraded network hardware such as Cisco routers and switches. READ FULL BIO >>
- How Quantum Computing Could Impact Everyday Laptops
- What Is The Difference Between Lenovo’s Pens? (with Part Numbers)
- Legion 5 Laptop Upgrade Guide: Game Like a Pro
- How to Replace Your Laptop Battery: A Step-by-Step Guide
- IdeaPad Gaming 3 Upgrade (Full Specs)
- Shut Down a Lenovo Laptop: Quick and Easy
Related: Best Business Laptop 2022